Summary: Access is a remote access service from Cloudflare. Cloudflare is a leading US based DNS, CDN and Website security solution provider. Cloudflare caters its services to more than 12 million applications and APIs. Cloudflare Access is proving to be a better replacement of the corporate VPNs in place. With Cloudflare Access, the customers can provide access to their website to the employees.
Access uses the authentication policies chosen by the customer, and thus keeps the user’s applications and website safe. With Access the customers no longer need to rely on the intranet and slow VPN connections. This provides better accessibility of the resources to the employees, and makes them as well as the company more efficient.
The snail’s pace of the VPNs paved way for Cloudflare to come up with Access

Conventionally, most of the bigger companies use the intranet to provide their employees access to the company’s resources such as files and applications. It is an effective way to share the resources and monitor the activities. But, as the enterprises got bigger, and the amount of data also increased in size, it became difficult to physically connect all the devices of the company to grant access to the employees.
Conventionally, most of the bigger companies use the intranet to provide their employees access to the company’s resources such as files and applications. It is an effective way to share the resources and monitor the activities. But, as the enterprises got bigger, and the amount of data also increased in size, it became difficult to physically connect all the devices of the company to grant access to the employees.
The enterprises turned to VPNs to counter this issue. Now they were able to connect various gateway systems of the intranet with one another, and also provide access to the remote devices and employees through the client. The VPNs come with strong encryptions and secure protocols, but this happens at the expense of speeds, and sometimes a lot of the speed is lost on the VPN.
“After all this hassle, users on the VPN are still highly susceptible to phishing, man-in-the-middle, and SQL injection attacks,” writes Venkat Vishwanathan, a Cloudflare engineer, in a blogpost. And he is absolutely right.
With the advent of cloud computing, and the increase in the mobility of devices as well as the employees, the companies needed to come up with secure ways to provide their offshore employees the ‘access’ to the necessary corporate resources. Clouflare Access is the one-stop solution to all these modern-day needs. It uses various authentication methods as intended by the customer to authorize access to offshore devices and employees.
Google did it first with BeyondCorp
Google came up with BeyondCorp to tackle this issue. They used the internet instead of the intranet to provide access to the company’s resources to the employees. It uses the concept of zero trust networks, and the users need to prove their identity before they are authorized to access the resources. Google is a big enterprise, and with the kind of resources they had at their disposal, this was a feasible solution for them.
“Cloudflare’s mission has always been to democratize the tools of the internet giants” writes Venkat, and they have achieved a great deal of success in this mission with Cloudflare Access. Cloudflare used a similar model and came up with Cloudflare Access. With the use of their existing servers, which are placed at various locations to provide DDoS protection and the CDN services, Cloudflare provides better accessibility and avoids slow traffic issues.
Cloud seems to be the limit for Cloudflare
Cloudflare was already into CDN services and DDoS mitigation before launching Cloudflare Access. They have more than 150 datacenters around the world, and it routes around 10% of the global internet requests. The existing knowledgebase and the resources made it easier for them to come up with a secure and reliable solution for the needs of the customers.
The customers can combine Access with other services of Cloudflare such as Argo to get better results. Argo analyzes the real-time traffic conditions and redirects the traffic through the fastest and reliable servers of Cloudflare. The fact that Cloudflare handles 10% of the global internet requests (more than 12 million properties) helps to get an accurate analysis.
A better and viable replacement of the corporate VPNs
The analogy that can be used in this context is that the VPN is equivalent to a fortress with a highly secure perimeter and all the company’s data is moved inside this secure fort. On the other hand, Cloudflare Access provides safes for storing this corporate data, which is also secure and tough to breach. The locks on these safes can be of various types as according to the wish of the customer. Just like the locks can be of multiple types, Cloudflare also provides various authorization options to be installed by the customers. Now, only those people will be able to open these locks who have suitable keys, and that is for the customer to take care of.
While the VPN uses various protocols and encryptions to avoid data breaching, Access uses HTTPS to secure all the connections.
Even though the VPN measures are very secure, it leaves the data flow at a snail’s speed. On the other hand, Access provides a swift connection with excellent security.
Takes complete care of the customer’s resources
When Cloudflare receives a request from a user to gain access to an Access enabled website or application, it checks if the visitor is allowed to proceed further based on the policies put in place by the customer or the enterprise.
For authorization and identification purposes, the customer can either use the identity providers such as Google, Otka, Facebook, Github, etc. or use the One Time Pin option available on the client. The customers also have the option to put multi-tier authentication process in place. TLS with client authentication can also be used to allow access to only those individuals and devices which have a unique client certificate.
Access allows the customers to come up with their customized access policies to protect the applications. Features such as session durations, allowed domains or subdomains can be specified to strengthen the security.
Cloudflare logs all the access to the customer’s website, and it can be monitored to find any unusual happenings. The administrator at the customer’s end can monitor all the devices which were granted access, what were the session durations, time stamps, the services accessed by the device. If there are any anomalies, the customer can respond right at the moment and withdraw the access to the device and the user.
In an interview with a news forum, Matthew Prince, co-founder, and CEO of Cloudflare mentioned that they are working to come up with anomaly detection tools which will notify the customer if there is any sort of unusual and anomalous activity which may deserve immediate attention.
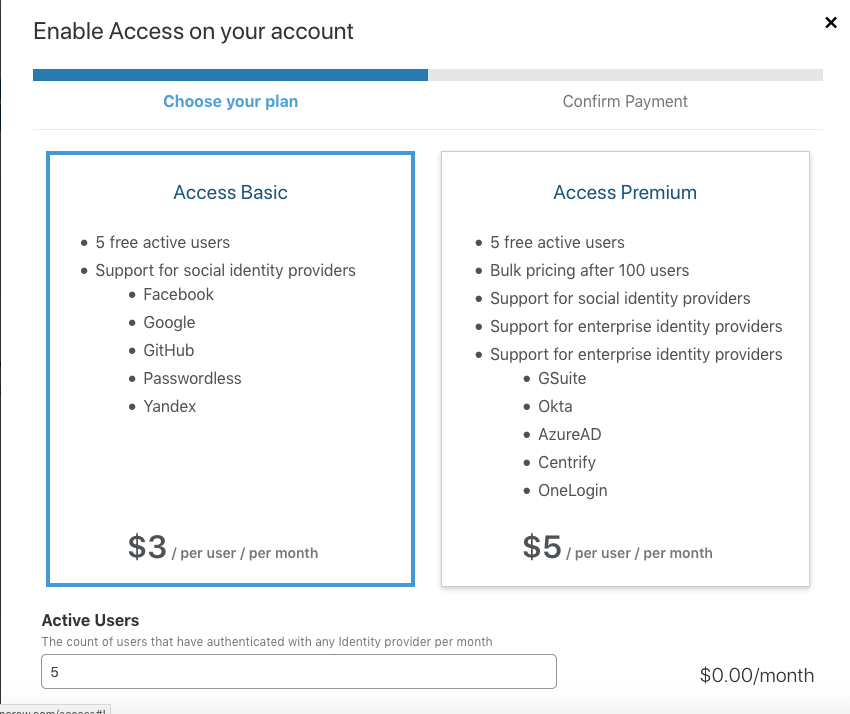
Individuals can try and use the service for free. The service is available for professional websites, businesses, and enterprises at different prices and you can also see how the service is different for these categories here.
