Privacy could be defined with several levels and depends on ourselves that how much privacy we require, and how much information we are willing to render freely. However, “walls have ears” must be upgraded with “network has eyes.” These are the eyes of the government, ISPs, hackers, cyber-frauds, competitors, and of millions who keep throwing a look over one knowingly or unknowingly.

That’s how the “virtual private network” comes in the picture acting as a shield to avoid these eyes. At the same time “Tor Browser” was also developed with the same motive. But, its limitations were discovered, and still one hundred percent privacy could not be claimed.
VPN is the technology that creates a safe data flow over a network by encrypting the data so that no one could understand even if he gets the access to that information. Tor uses the same methodology of encryption but in addition, the data has multiple layers of encryption, and the flow is not a direct one, but through different nodes about which one will explore in the latter section.
Why data breaches occur?
So question is, why even after the advanced encryptions and high-level encapsulation data breaches occur?
Breaking the key is a tough task, but stealing it isn’t. Using a VPN can make sure that the key won’t be broken, nor it will get stolen.
However, the data one has shared might be accessible by the VPN provider if it keeps logs, and puts a track of one’s activities. When it comes to the Tor, it isn’t safe for the complete process of sending and receiving data. Even the use encryption gets compromised in Tor. Hence, there is an exigency of a more secure connection.
Breaking the key is a tough task, but stealing it isn’t. Using a VPN can make sure that the key won’t be broken, nor it will get stolen. However, the data one has shared might be accessible by the VPN provider if it keeps logs, and puts a track of one’s activities. When it comes to the Tor, it isn’t safe for the complete process of sending and receiving data. Even the use encryption gets compromised in Tor. Hence, there is an exigency of a more secure connection.
What if we combine both Tor and VPN?
That sounds like a good idea, but the practical use of it develops new limitations. Recommending its usage would only be there when one learns about the multiple layers of encryption that could be acquired by adding the layers of encryptions of Tor and VPN.
However, “more is not always better,” but it may create a completely different product which could be configured in two different ways:
- Tor over VPN: First connection-VPN, Second connection-Tor
- VPN over Tor: First connection-Tor, Second connection-VPN
They might appear alike, but they aren’t, and these two combinations provide a completely different outcome, advantages, and disadvantages.
One knows now that establishing a secure connection has four different ways:
- Connection with VPN
- Connection with Tor
- Connection with Tor over VPN
- Connection with VPN over Tor
However, for assimilation that exists among all is unrivaled (if there is any), one requires to understand the working for every kind of connection.
Connect with VPN
VPN technology is used all over the world for occasionally accessing the banned content, sometimes for hiding the true IP, and at times for performing illegal activities also. The security of the connection utterly depends upon the VPN provider.
Initially, one needs to install a VPN client in the device. After that, whenever one turns it on, the data passes through the client where it gets encrypted with the help of a secret key. Depending on the encryption, the data is encrypted it with multiple rounds. If the encryption is strong, and with multiple rounds then it commits a high level of security. However, just a spark is required to cause the fire, and data leakage could occur within seconds even through a single element of the complete process. There could be threat developments through the protocol, DNS and no logging policy.
A good VPN provider must have:
- Encryption: AES encryption with a 256-bit key.
- Protocol: OpenVPN for the most secure network.
- DNS: Provider must not allow any involvement of third-party DNS.
- NAT firewall.
- Killswitch
- More the servers, better the VPN provider.
- And the most important one, No log policy.
Because of the limitations that the VPN holds, like sharing the information with the VPN provider or with third-party DNS compromise the security. There was and has always been a need for a technology where one never need to trust someone, and which is free of anyone’s control. Tor is one such technology which is supported by thousands of volunteers all over the world. Currently, the Tor Project, a research-education nonprofit organization sustains and develops Tor Browser.
But is the Tor browser eliminates all the drawbacks of VPN?
OR
Does it involve some different limitations?
Tor browser provides better anonymity in comparison of many VPN solutions. It is because unlike VPN, it doesn’t require any provider with whom one needs to share the data. In VPN’s case, provider or the DNS would be keeping the logs, and there have been times when VPN providers have rendered information to the government as the law bounds everyone.
Connection with Tor
Tor has a slightly complicated connecting technique which has multiple layers of encryption. The encryption used by the Tor is RSA 1024 which commits the comparable level of security that AES 256 offers. Tor is available on the Internet in the form of Tor Bundle which requires less configuration and provides more ease.
- Initially one needs to download the Tor Bundle and install Tor Browser in the system.
- As we already know that Tor doesn’t require any provider, and it has a network of its own so one can directly start using it.
- After one enters a domain name or do a search through Tor, tor searches for the Entry Node (also known as Guard Node). Entry node is the first server that the Tor selects randomly. After the selection of server, the Tor sends a “create” request, and the server will respond “created” to it. After this a bridge is built between the system, and node 1 or the Entry Node. A session key is exchanged between the Tor and node 1. This session works to remove the upper layer of the encryption.
- After that node 1 searches for the second server which acts as a middle node or node 2. The node 1 sends “create” request to node 2 and gets “created” as the response. Now again, the exchange of session key takes place, but between Tor and node 2. This key works to remove the middle layer of the encryption.
- The same thing is followed for Exit node which is the 3rd node of the path. Node 2 sends the “create” request, and node 3 replies with “created.” Exchange of session key takes place between Tor and node 3.
- The data is then transmitted from the system → Entry Node→ Middle Node→ Exit node→ Destination Server. When the data reaches to node 3, it is again transmitted to the system to confirm if the data is the same or not. After the confirmation, the unencrypted data travels out of the exit node and reaches to the destination server.
- When data goes out of the system, it has three layers of encryption like of an onion, and that’s why Tor is also known as Onion Router. As it reaches to passes from node 1, the other most layer of the encryption is removed. After it passes through node 2, one more layer is decrypted using the session key. When, through Entry node data pass, it gets converted into plaintext, exactly same with the data which was converted. When it travels from the 3rd server to the destination file, it acts the decoded text and here where the problem arrives.
Selection of path from system to Entry node is acceptable as it ensures a secure data transfer. The node 1 knows the IP address of the system, but it does not know what the encrypted data is. One could discover the origin of data if the security of node 1 is compromised. Node 2 does not know about the origin, destination and what’s encrypted. If one talks about node 3, it knows about the destination, but that isn’t the concern. Even if the origin of data can’t be identified through node 3, yet the plaintext could be obtained easily. If the data contains personal information such as credit card details or identification number, they could be obtained easily by the hacker at the exit node. When one starts using Tor, he is completely anonymous, but with every data, he provides the anonymity decreases.
Tor, due to this chain of servers, may sometime deliver a very low speed, and though one doesn’t need to think about “no logging policy,” he got other ways from where data could get leaked.
What if a combined connection of Tor and VPN is established?
It’s universally known that one plus one is two, but not in this case. Tor’s anonymity and VPN’s privacy don’t add up to create a more secure network, but they create a different kind of network for sure. If VPN is connected first and latter Tor, it’s called Tor over VPN, and if Tor connects first and latter VPN, then it’s called VPN over Tor.
So, which network is better among these two?
The answer to this is no one. Both the networks have their separate limitations and advantages, and thus, must be utilized according to the requirement and the location, or else the government agents will be there at the door, very next moment.
When one connects the VPN first, all the data gets encrypted, and all the process takes place through the private network that is separated from the rest of the internet. If the case is reversed, and Tor has connected first, and after VPN the encryption, the encryption through VPN takes place after the third node.
Working of Tor over VPN
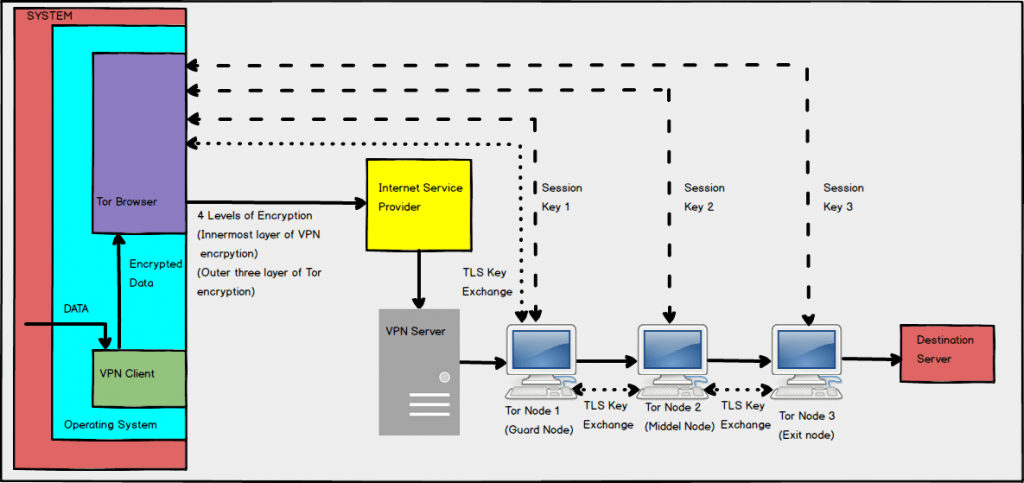
This adds an extra layer of VPN encryption in addition to the three layers of Tor. This provides security from the ISP and allows one to visit to hidden Tor services. It is beneficial when it comes to enhancing one’s anonymity level. VPN provider would never know about one’s activity details due to the Tor’s three encryption levels. However, if one looks at the limitation side, VPN provider would know about the true IP address. One may end up with a blocked exit node, and no further data flow will take place. Apart from this, it will also make one’s system slow to some extent:
Tor over VPN data transfer speed = Speed after connecting with VPN client/ Original speed X Speed experienced through Tor Browser
This reduction completely depends on the VPN provider as the Tor speed remains the same because it owns its network which works uniformly all over the world.
The data path length remains the same, only the level of encryption increases. The data flow in Tor over VPN occurs in this way:
- The data one enters in Tor will pass through the VPN client and gets encrypted first.
- With Tor, it will pass through ISP, and reaches to VPN server.
- From there, it will reach to Node 1, and the data flow will occur from Node 1 to Node 2 to Node 3.
- The last level of Tor encryption will be removed. However, we are not sure about the VPN encryption. Probably, it should be still there as it has not reached to its destination server, and all the process is going inside the VPN.
- From node 3, it travels to destination server where the one wanted to deliver the data.
These could be useful when one is concerned about one’s ISP knowing that one is using Tor because it won’t be knowing it after one adds VPN and it also helps to hide one’s true IP by substituting it with VPN server’s IP. However, there is one another way, in which it could be configured, and that is VPN over Tor.
Working of VPN over Tor
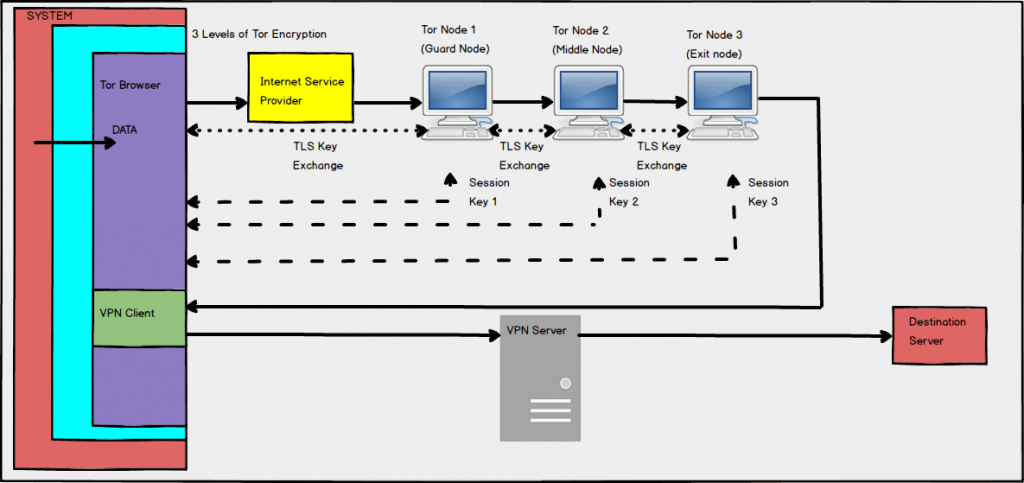
Not all the VPN providers offer this configuration. The only one known to us is AirVPN which offers VPN over Tor. It is not as easy as Tor over VPN, but worthy of saving our true IP which is not even visible to the VPN provider also. No VPN provider could see our true location if we could implement VPN over Tor. This helps one not to put trust on any other party (here VPN provider) about one’s activity. Again, how the data flow occurs in this case?
- The data flows from Tor to node 1 to node 2 to node 3, same as it happens in Tor without VPN. In this, case, one’s ISP would be knowing that he is using Tor.
- At the exit node, VPN client encrypts the data and forwards it to the VPN server. It helps to bypass the blocked exit node.
- From the VPN server, the data reaches to the destination server.
But this has many limitations in comparison of Tor over VPN. The major ones are this that one can’t excess the hidden services of Tor due to no VPN encryption. Also, it makes us insecure to the global end-to-end timing attacks which not only de-anonymize a user but could also harm and leak its data.
So, now we know about all the four combinations. VPN could be used, but then one needs to have a trustable VPN provider who has “No Logging Policy.” If it’s not keeping any logs, there is nothing to worry about. Also, one will not be allowed to access Tor’s hidden services with any other browser. That’s why, for access all the Internet content, and to be anonymous, using Tor is important. Now, Tor can also be used, with a VPN provider in two different ways. One already knows that the end node is vulnerable, and if anyone is keeping an eye on the end node, then one’s data could be leaked. However, they will never know that from where the data arrived or who generated the data. That’s why using Tor is the best option if used carefully. Do not provide any personal information while one visits any website with Tor. Now, if one wishes to access the hidden services, one needs to use Tor over VPN, but in that case, one will reveal his true IP. Using Mullvad VPN would be the best idea as it doesn’t ask for any personal information during signup. Also, they don’t log any activity. However, I would not suggest using VPN over Tor because it may cause hacking of one’s data due to global end-to-end timing attacks.
It completely depends upon one’s requirement that which combination suits him. If one needs to use the geo-restricted internet without revealing his IP address, a trustable VPN provider would be the best idea. However, if one doesn’t wish to put faith in some third-party, use Tor. If one is still not willing to share the information that the user is using Tor to the ISP, use it with a trustable VPN provider who could keep one anonymous. However, I would never suggest the last option: VPN over Tor.
